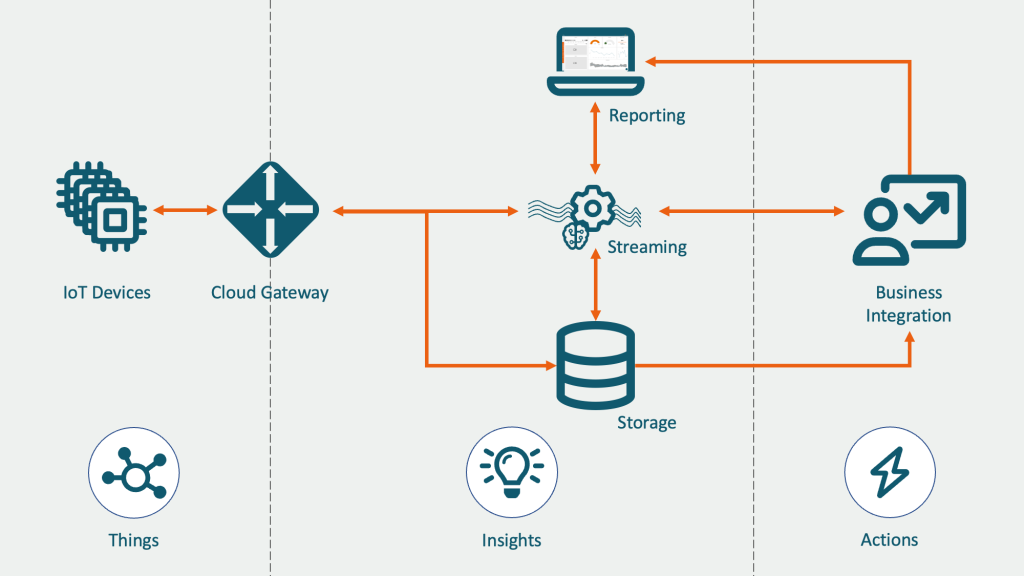
In today's rapidly evolving technological landscape, P2P IoT devices have become a focal point of innovation, transforming the way devices communicate and interact. Peer-to-peer (P2P) IoT systems eliminate the need for centralized servers, offering a more decentralized and efficient approach to connectivity. This shift not only enhances scalability but also ensures robust security and reliability.
As industries increasingly adopt IoT technologies, understanding the intricacies of P2P IoT devices becomes crucial for businesses and individuals alike. These systems play a pivotal role in enabling seamless communication between devices, fostering an interconnected world where data is shared efficiently and securely.
This article delves deep into the world of P2P IoT devices, exploring their functionality, benefits, challenges, and future prospects. By the end of this guide, you'll gain a comprehensive understanding of how P2P IoT devices are shaping the future of technology and connectivity.
Read also:Exploring The World Of Animation By Maplestar A Comprehensive Guide
Table of Contents
- Introduction to P2P IoT Devices
- P2P IoT Architecture
- Benefits of P2P IoT Devices
- Challenges in Implementing P2P IoT
- Security in P2P IoT Systems
- Real-World Use Cases of P2P IoT Devices
- The Future of P2P IoT Devices
- P2P vs Centralized IoT Systems
- Standards and Protocols for P2P IoT
- Conclusion
Introduction to P2P IoT Devices
What Are P2P IoT Devices?
P2P IoT devices represent a paradigm shift in how connected devices operate. Unlike traditional IoT systems that rely on centralized servers, P2P IoT devices enable direct communication between devices without an intermediary. This architecture reduces latency, enhances efficiency, and minimizes the risk of single points of failure.
The growing demand for real-time data exchange and decentralized networks has fueled the adoption of P2P IoT technologies. These devices are instrumental in creating smarter, more resilient ecosystems, making them ideal for applications ranging from smart homes to industrial automation.
Key Features of P2P IoT Systems
P2P IoT systems are characterized by several key features that distinguish them from centralized architectures:
- Decentralization: Devices communicate directly without the need for a central server.
- Scalability: The system can handle a large number of devices without compromising performance.
- Resilience: Eliminates the risk of system-wide failures caused by a single point of failure.
- Efficiency: Reduces latency and bandwidth usage by enabling direct communication.
P2P IoT Architecture
The architecture of P2P IoT devices is designed to maximize efficiency and reliability. This section explores the fundamental components and principles that underpin P2P IoT systems.
Key Components
A typical P2P IoT architecture consists of the following components:
- Nodes: Devices that participate in the P2P network, capable of both sending and receiving data.
- Network Protocols: Standards that govern how devices communicate and exchange data.
- Data Storage: Decentralized storage mechanisms that ensure data availability and integrity.
Operating Principles
P2P IoT systems operate on principles such as:
Read also:Greg Gutfeld Illness Understanding The Impact On His Career And Life
- Peer Discovery: Identifying and connecting to other devices in the network.
- Data Synchronization: Ensuring all nodes have access to the latest data.
- Security Protocols: Implementing measures to protect data and maintain privacy.
Benefits of P2P IoT Devices
P2P IoT devices offer numerous advantages over traditional IoT systems. This section outlines the key benefits that make P2P IoT technologies a preferred choice for modern applications.
Enhanced Scalability
P2P IoT systems are inherently scalable, allowing them to accommodate a growing number of devices without performance degradation. This scalability is crucial for large-scale deployments in industries such as logistics and manufacturing.
Improved Security
By eliminating centralized servers, P2P IoT systems reduce the risk of data breaches and cyberattacks. The decentralized nature of these systems ensures that even if one node is compromised, the entire network remains secure.
Cost Efficiency
P2P IoT devices eliminate the need for costly infrastructure, such as centralized servers and data centers. This cost efficiency makes them an attractive option for businesses looking to optimize their IoT investments.
Challenges in Implementing P2P IoT
Despite their numerous advantages, P2P IoT systems face several challenges that need to be addressed for widespread adoption. This section explores the key challenges associated with P2P IoT devices.
Complexity in Deployment
Deploying P2P IoT systems can be complex, requiring specialized knowledge and expertise. The decentralized nature of these systems demands careful planning and execution to ensure optimal performance.
Interoperability Issues
Ensuring interoperability between different P2P IoT devices and systems remains a challenge. Standardization efforts are underway to address this issue, but it continues to pose a barrier to seamless integration.
Resource Constraints
P2P IoT devices often operate on limited resources, such as power and bandwidth. Optimizing resource utilization while maintaining performance is a critical challenge in P2P IoT implementations.
Security in P2P IoT Systems
Security is a top priority in P2P IoT systems, given the sensitive nature of the data exchanged between devices. This section examines the security measures implemented in P2P IoT technologies and their effectiveness.
Encryption Techniques
Encryption plays a crucial role in securing P2P IoT communications. Advanced encryption algorithms are employed to protect data integrity and confidentiality, ensuring that only authorized devices can access and interpret the information.
Authentication Mechanisms
Robust authentication mechanisms are essential for verifying the identity of devices in a P2P IoT network. These mechanisms help prevent unauthorized access and ensure that only legitimate devices can participate in the network.
Intrusion Detection Systems
Intrusion detection systems (IDS) are deployed to monitor P2P IoT networks for suspicious activities. These systems alert administrators to potential threats, enabling timely responses to mitigate risks.
Real-World Use Cases of P2P IoT Devices
P2P IoT devices are being deployed across various industries, driving innovation and enhancing operational efficiency. This section highlights some real-world use cases of P2P IoT technologies.
Smart Homes
P2P IoT devices are transforming the smart home landscape by enabling seamless communication between appliances, lighting systems, and security devices. This interconnected ecosystem enhances convenience and energy efficiency for homeowners.
Industrial Automation
In industrial settings, P2P IoT devices facilitate real-time monitoring and control of machinery, optimizing production processes and reducing downtime. The decentralized nature of these systems ensures robust performance even in challenging environments.
Healthcare
P2P IoT devices are revolutionizing healthcare by enabling remote patient monitoring and data exchange between medical devices. This technology enhances patient care and supports more informed decision-making by healthcare professionals.
The Future of P2P IoT Devices
The future of P2P IoT devices looks promising, with ongoing advancements in technology and increasing adoption across industries. This section explores emerging trends and potential developments in the P2P IoT space.
Advancements in Blockchain Technology
Blockchain technology is being integrated into P2P IoT systems to enhance security and transparency. This integration enables secure and tamper-proof data exchange, further strengthening the reliability of P2P IoT networks.
Artificial Intelligence Integration
Artificial intelligence (AI) is being incorporated into P2P IoT devices to improve decision-making and automation capabilities. AI-driven P2P IoT systems can analyze vast amounts of data in real-time, enabling predictive maintenance and optimized performance.
5G and Beyond
The rollout of 5G networks is set to revolutionize P2P IoT connectivity by providing ultra-low latency and high-speed data transfer. This advancement will unlock new possibilities for P2P IoT applications, paving the way for more innovative use cases.
P2P vs Centralized IoT Systems
Understanding the differences between P2P and centralized IoT systems is essential for making informed decisions about technology adoption. This section compares the two architectures based on key parameters.
Performance
P2P IoT systems generally outperform centralized systems in terms of speed and efficiency, thanks to their decentralized architecture. However, centralized systems may offer better control and management capabilities in certain scenarios.
Scalability
P2P IoT systems are more scalable than centralized systems, as they do not rely on a single server to handle all communications. This scalability makes them ideal for large-scale deployments where performance consistency is crucial.
Security
Both architectures have their own security advantages and challenges. P2P systems eliminate single points of failure, while centralized systems offer centralized control and monitoring capabilities. The choice between the two depends on specific use case requirements.
Standards and Protocols for P2P IoT
Standardization is critical for ensuring interoperability and consistency in P2P IoT systems. This section discusses the key standards and protocols that govern P2P IoT technologies.
IEEE Standards
The Institute of Electrical and Electronics Engineers (IEEE) has developed several standards for IoT devices, including those for P2P communication. These standards provide guidelines for device interoperability, security, and performance.
MQTT Protocol
The Message Queuing Telemetry Transport (MQTT) protocol is widely used in IoT systems, including P2P architectures. It enables lightweight and efficient communication between devices, making it suitable for resource-constrained environments.
CoAP Protocol
The Constrained Application Protocol (CoAP) is another protocol commonly used in P2P IoT systems. It supports RESTful interactions between devices and is designed for low-power and low-bandwidth networks.
Conclusion
P2P IoT devices are at the forefront of technological innovation, offering a decentralized and efficient approach to connectivity. This comprehensive guide has explored the architecture, benefits, challenges, and future prospects of P2P IoT systems, providing valuable insights for businesses and individuals alike.
We encourage you to share your thoughts and experiences with P2P IoT devices in the comments section below. Additionally, feel free to explore other articles on our site for more information on emerging technologies and trends. Together, let's shape the future of connectivity!
References:
- IEEE Standards Association. (2023). https://www.ieee.org
- O'Malley, S. (2022). The Future of IoT: Trends and Predictions. https://www.techradar.com
- Smith, J. (2023). P2P IoT Security: Best Practices and Guidelines. https://www.securitytoday.com